Company Continuity Assurance: Your Trusted Partner in Corporate Security
Tailored Corporate Protection Solutions for Your One-of-a-kind Company Demands
In today's significantly complicated service landscape, making certain the safety and security of your organization is of paramount importance., we acknowledge that every service has its own special collection of safety and security needs. That is why we offer tailored business protection remedies made to attend to the certain difficulties and vulnerabilities of your company.
Examining Your Particular Safety And Security Needs
To effectively address your company's protection problems, it is critical to conduct an extensive evaluation of your details protection demands. Recognizing the unique risks and vulnerabilities that your organization faces is important for developing an efficient protection approach. Without a proper analysis, you may allocate resources inefficiently or ignore critical areas of susceptability.
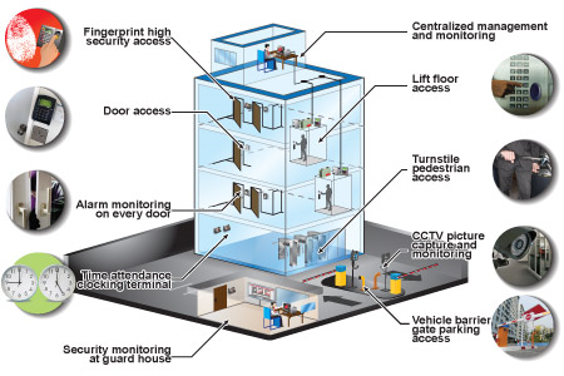
The very first step in analyzing your certain safety and security demands is to perform a complete assessment of your physical properties, consisting of buildings, parking areas, and gain access to factors. Additionally, it is essential to analyze your organization's electronic safety and security by examining your network facilities, information storage, and security procedures.
One more essential aspect of examining your protection requires is comprehending your company's unique functional demands and conformity commitments. This consists of thinking about elements such as the nature of your sector, the value of your possessions, and any type of governing or legal requirements that might use. By recognizing these certain aspects, you can customize your security gauges to satisfy the specific demands of your business.
Tailoring Security Equipments for Optimum Defense
Tailor your monitoring systems to supply ideal protection for your company. A one-size-fits-all strategy just won't be adequate when it comes to securing your business and its properties. Every organization has its very own special safety and security requirements, and customizing your security systems is crucial to ensuring that you have one of the most efficient protection in place.
Primarily, it is necessary to conduct a thorough evaluation of your facilities to recognize at risk locations and possible protection dangers. This will certainly help identify the kind and number of video cameras required, along with their calculated positioning. High-risk locations such as entrances, parking area, and storage centers may call for more advanced surveillance modern technology, such as high-resolution cams or evening vision abilities.

Incorporating your surveillance systems with other safety actions, such as access control systems or alarm, can additionally improve the effectiveness of your total protection method. By personalizing your monitoring systems to line up with your certain organization demands, you can have comfort recognizing that your customers, possessions, and workers are shielded to the greatest degree possible.
Applying Tailored Gain Access To Control Steps
For ideal security, companies need to apply customized accessibility control procedures that straighten with their distinct service demands. Access control actions are crucial in securing delicate info and making sure that only licensed people have accessibility to particular locations or resources within a company. By customizing access control actions, business can establish a durable protection system that effectively minimizes threats and safeguards their possessions.
Implementing customized gain access Continued to control measures entails a number of essential steps. Initially, an extensive assessment of the company's safety and security demands and prospective vulnerabilities is required. This assessment must think about factors such as the nature of the organization, the worth of the information or properties being shielded, and any kind of regulative or conformity demands. Based on this assessment, companies can after that figure out the suitable gain access to control devices to implement.
Accessibility control actions can include a mix of physical controls, such as badges or keycards, in addition to technical options like biometric verification or multi-factor authentication. These measures can be executed across numerous access points, such as doors, gates, or computer systems, depending upon the business's certain needs.
Furthermore, firms should establish clear policies and treatments concerning gain access to control. This includes defining duties and roles, setting up customer accessibility degrees, consistently reviewing access opportunities, and monitoring accessibility logs for any kind of dubious tasks. Normal training and recognition programs need to additionally be performed to make certain workers are mindful of the value of gain access to control and stick to developed procedures.
Enhancing Cybersecurity to Secure Sensitive Information
Implementing robust cybersecurity procedures is essential to successfully guard sensitive data within a company. In today's digital landscape, where cyber threats are becoming progressively sophisticated, organizations need to prioritize the defense of their valuable details. Cybersecurity encompasses a variety of techniques and innovations that aim to prevent unapproved gain access to, information breaches, and other destructive tasks.
To boost cybersecurity and protect delicate information, business need to implement a multi-layered technique. Furthermore, carrying out solid access controls, such as multi-factor authentication, can assist protect against unauthorized access to delicate systems and information.

Furthermore, companies ought to have a case reaction plan in position to effectively react to and alleviate any type of cybersecurity incidents. This strategy must detail the steps to be absorbed the event of a data breach or cyber strike, consisting of communication methods, control procedures, and healing strategies.
Recurring Assistance and Maintenance for Your Distinct Requirements
To ensure the continued efficiency of cybersecurity procedures, continuous assistance and maintenance are essential for resolving the advancing risks encountered by services link in protecting their delicate information. In today's quickly altering electronic landscape, cybercriminals are continuously discovering brand-new means to make use of susceptabilities and breach safety systems. Consequently, it is vital for organizations to have a robust assistance and maintenance system in area to remain ahead of these hazards and protect their valuable details - corporate security.
Ongoing support and maintenance entail consistently upgrading and patching safety software program, keeping an eye on network activities, and conducting vulnerability evaluations to recognize any kind of weak points in the system. It also includes offering prompt assistance and support to staff members in carrying out security finest techniques and replying to potential safety occurrences.
By investing in continuous assistance and upkeep services, businesses can take advantage of proactive tracking and discovery of possible threats, along with prompt feedback and remediation in case of a safety breach. This not just helps in lessening the impact of a strike however also ensures that the company's security pose remains adaptable and strong to the developing danger landscape.
Final Thought
To properly resolve your organization's safety issues, it is important to conduct an extensive evaluation of your details safety demands. Every business has its very own unique safety and security needs, and customizing your monitoring systems More hints is crucial to making certain that you have the most effective protection in area.
For ideal protection, companies should apply tailored access control procedures that align with their one-of-a-kind company demands.In conclusion, tailored business safety remedies are essential for organizations to address their unique protection needs. By examining specific safety requirements, personalizing security systems, applying tailored gain access to control steps, and improving cybersecurity, companies can secure and protect delicate data against possible risks.